[Tutorial] How to get Allegro passwords
- Get some game on Allegro engine
- Check with Grabber tool if archives are password protected.
- Check on the xentax wiki if the password was already cracked by someone else https://wiki.xentax.com/index.php/Allegro_DAT
- If the password is still unknown, then open IDA Pro
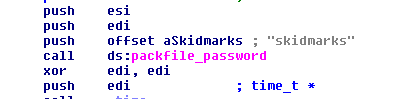
- Search for string „packfile_password” in the assembler code.
- Go to address where you have instruction like „call ds:packfile_password”.
- Password for DAT archive will be above that instruction
8. Now check the password in Grabber tool if it works
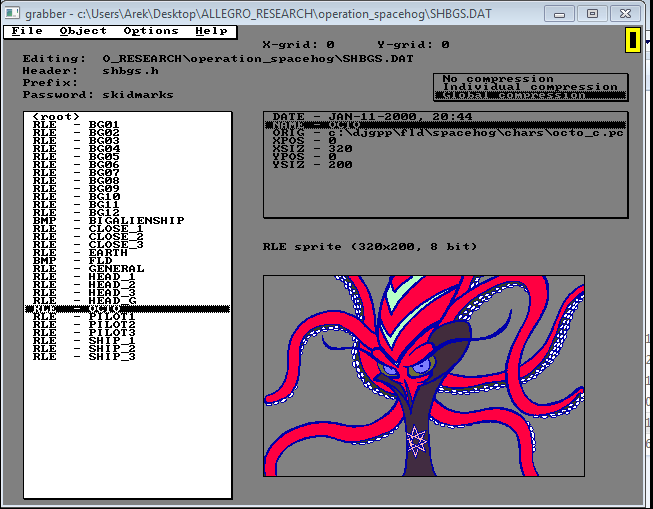
9. If you can see some assets in the preview, then your password is correct.
10. That’s all. Happy modding. 🙂
Notes:
1. Sometimes password won’t be in plain text. In this case you have to set a breakpoint on „call ds:packfile_password” and see what password is passed to the function.
2. You can also use sysinternal’s string tool to export all strings from EXE and look for password there.
UPDATE – 21.07.2024
I have created new frida script today that will make getting Allegro password much easier.
It’s available on my github here:
https://github.com/bartlomiejduda/Tools/blob/master/NEW%20Tools/Allegro/allegro_DAT_frida_hook.js
You have to install frida first:
pip install fridaThen script can be used like this:
frida.exe -f <game_exe> -l <script_name>For example:
frida.exe -f HoH.exe -l allegro_DAT_frida_hook.jsExample result below:
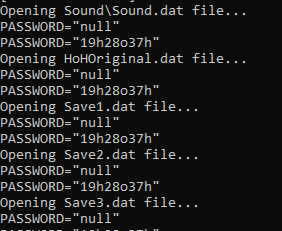
„Sometimes password won’t be in plain text. In this case you have to set a breakpoint on „call ds:packfile_password” and see what password is passed to the function.”
Could you please clarify what you mean by „see what password is passed to the function”?
Sure. I’ll explain. In some games (like „Alex the Allegator 4” if I remember correctly) you have to debug game’s code to find a valid password. You can use programs like „IDA PRO”, „Ghidra” or „x32dbg” to set a breakpoint at a specific line of code and then you have to follow this code to some other function that should be responsible for generating a password from the code. When you’ll find it, you just have to watch registers or memory to see the plain text password in the debugger.
Noted! How exactly do I go about following the code to that other function, though? (I’m using IDA Pro)
You need to use debugger. IDA has one built-in debugger called WinDbg, but you can probably configure some more. You can also use something like retsync https://github.com/bootleg/ret-sync to synchronize your debug session from other tool like x32dbg with IDA.
Debugging games hasn’t been covered deeply in any of my tutorials yet, but you can also check out some tutorials available on ResHax https://reshax.com/topic/47-reverse-engineering-tutorials-collection/
Concerning the game 'Head over Heels’
Trying to load up HoHOriginal.dat in the Grabber tool with the password „19h28o37h” gives me this error: „Error reading [my directory]\HeadOverHeels\HoHOriginal.dat”
It seems that the only datafile used by the game that’s able to be loaded in the Grabber tool with this password is Sound.dat. I haven’t been able to find a password for HoHOriginal.dat (even after many hours of messing around in IDA Pro).
No, typing „null” as the password didn’t work either.
The password you provided is the only password used by the game. I double checked.
So the game has to use some additional layer of protection. Try to dump decrypted archive from memory and then use this password with Grabber tool.